Summary
At its core, SecurEnds was built around performing reviews at a user level. However, there are some alternate solutions that can be taken to leverage existing functionality to review permissions associated to roles or groups. The premise is built around creating a user (or “pseudo-user”) to represent the group/role. The specific permissions for that group/role are then added to this pseudo-user as entitlements. This allows for reviewing of the permissions at the entitlement level when performing a campaign. Depending on the number of role/group owners that will be performing the review, configuration will need to be adapted appropriately within the SecurEnds tool. Below are the steps for setting up the system for different scenarios.
A Single Role/Group Owner for an Application
If an application has a single role/group owner, then one pseudo-user can be utilized in the system. This user will represent the application level pseudo-user that will then have the group/role credentials and permission assigned to it.
- For a single pseudo-user, they can be added directly to the People tab and the appropriate fields populated. (NOTE: For the below examples, Active Directory is the application that is being used to demonstrate the process so the pseudo-user information being used reflects that)
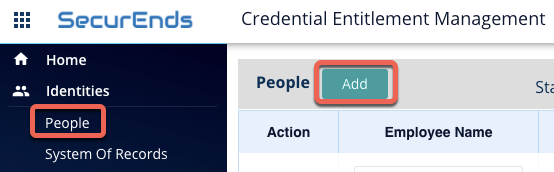
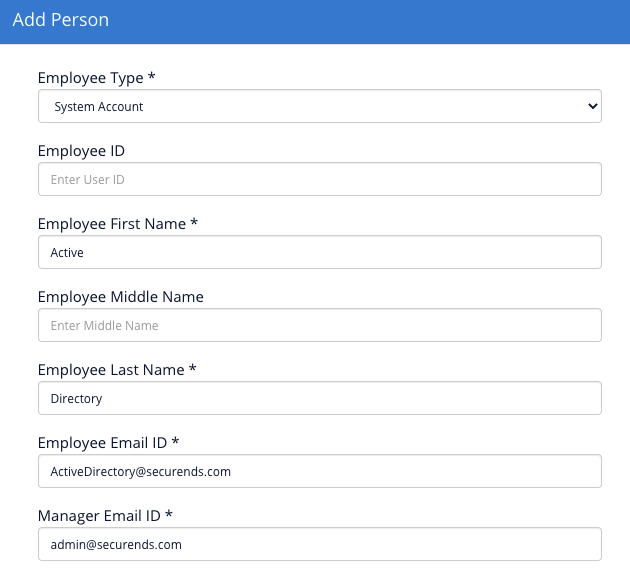
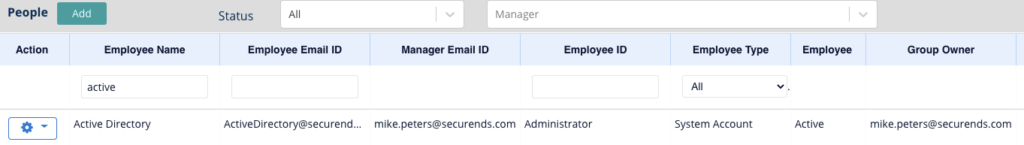
- Once this user has been added they can be viewed in the system from the People tab
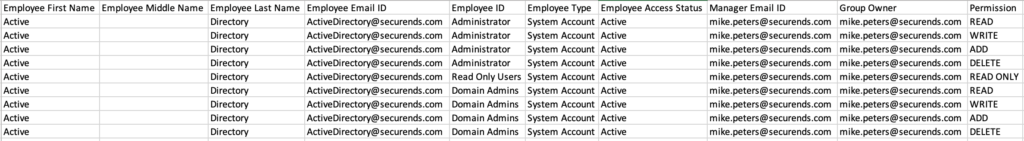
- The next step is to utilize the sample CSV file provided within the SecurEnds tool to create credential records to assign to the newly created pseudo user. The first and last name will be the same as the pseudo-user but the Employee ID will reflect the name of the group/role. The Group Owner will also remain the same, and should correlate to the role/group owner that will be performing the review. A “Permission” column will also need to be added, and a separate line included for each permission that is being reviewed.
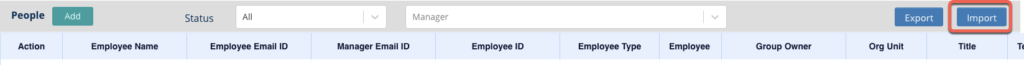
- Import this CSV file to the People tab and map the columns appropriately.
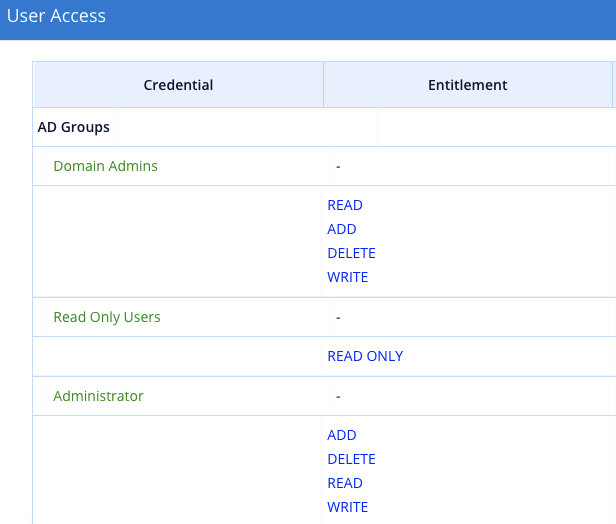
- The credentials (representing the groups) as well as their permissions will now be assigned to the pseudo-user.
- If roles/groups are to be reviewed at the same time as the users of the application, be sure to add this pseudo user to the application CSV going forward. This will ensure it is included in the scope of the campaign. If the roles/groups are reviewed separately from the users in the campaign, create a separate application that includes just the pseudo-user and have that application included in the campaign template.
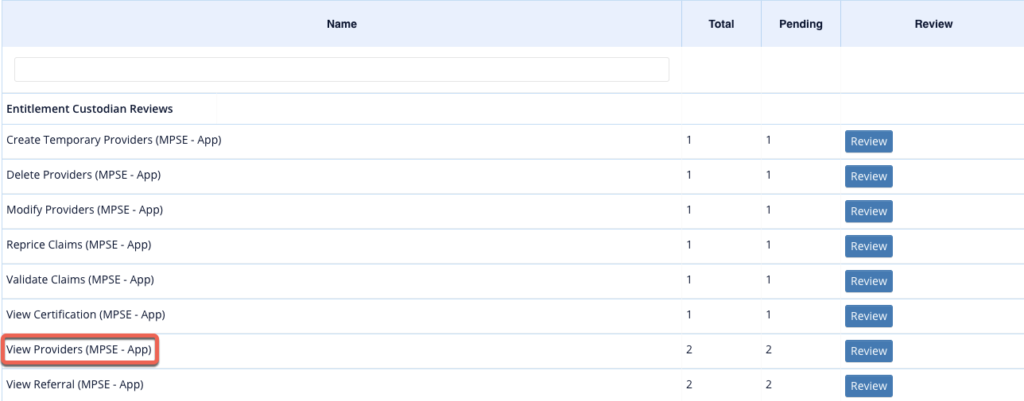
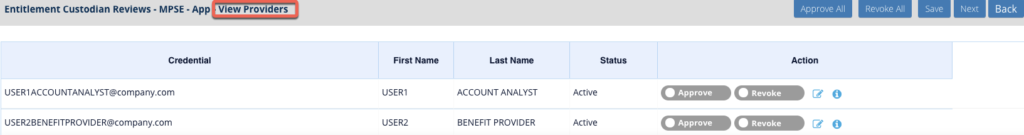
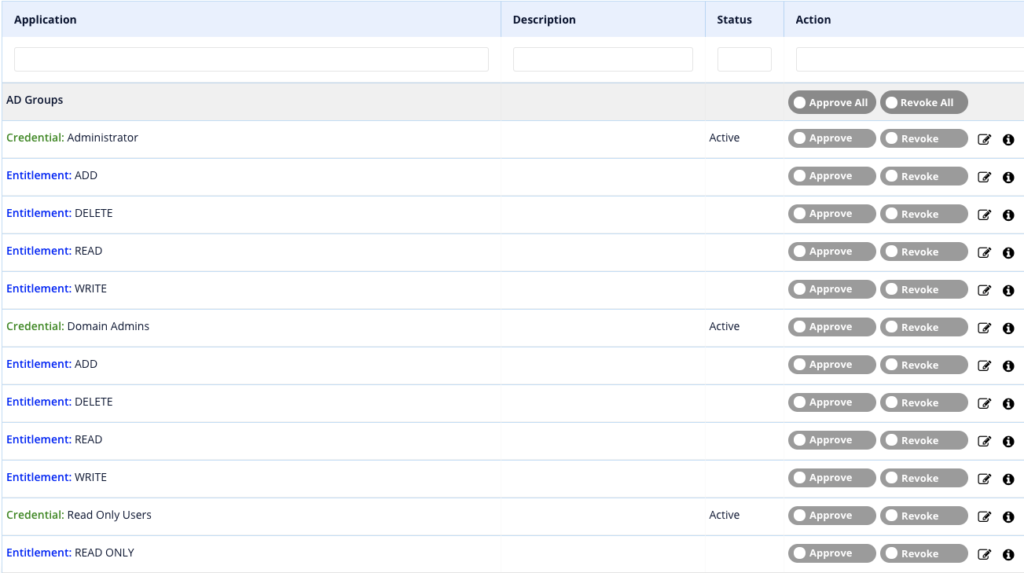
- Below is an example of what it looks like when reviewing the above added user. Each permission has its own approve/revoke option to allow for individual reviewal.
Multiple Role/Group Owners for an Application
For the use case where there are multiple role/group owners that will be performing the review, the steps are very similar, but the credentials cannot be assigned to a single pseudo-user. Instead, each of the credential records need to be created as separate pseudo-users and included in the application being reviewed. This is to allow for each role/group based pseudo-user to be assigned accordingly to the appropriate role/group owner.
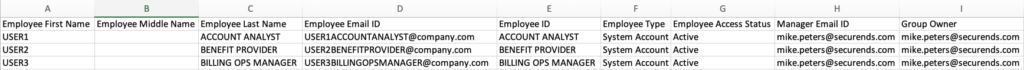
- The first step is to utilize the sample CSV file provided within the SecurEnds tool to create a CSV that contains each group/role represented as a pseudo-user.
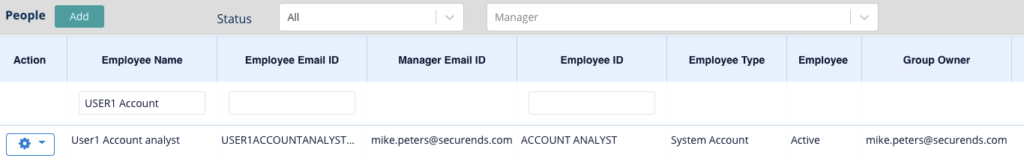
- This CSV can then be imported into the “People” tab to create these pseudo-users in the system.
- A separate SOR can also be created and the CSV imported using that method if that is preferred.
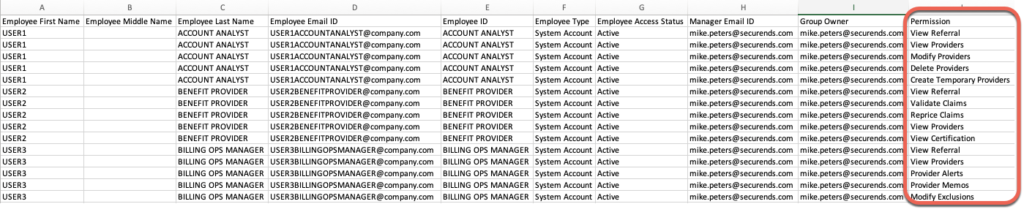
- These users then need to also be added to the Application CSV, with each entitlement as a separate line item.
- NOTE: Be sure to assign the appropriate Manager, Entitlement Owner/Custodian, or Application Custodian depending on who will be responsible for reviewing these group/role pseudo-users.
- With the pseudo-users now a part of the application, they will be a part of the campaigns and the groups/roles can be reviewed as individual elections.